In today's article we will talk about programming. More specifically, we will program a small utility to hide / protect your important files (passwords, important memories ... etc).
Little notes before you start:
This utility is written in VB.NET language, it is an old project brought up to date.
This utility is only available on Windows.
For starters, and to edit the source code, you will need to install Visual Studio Community (the integrated development environment of Microsoft).
You will also need to install the .NET Framework, version 3.5 minimum (normally already present on most PCs). And you will need a minimum of knowledge in VB.NET language (or want to learn and understand;)).
Want to learn programming to get started on your own projects right now? Download the complete guide to learn C, C # and Python? Click here. Use the promo code "FIRSTAPROG" to get it at -20% (8 codes remaining).
What is a FileProtector?
It is a utility to protect your sensitive files with a password. This type of tool already exists, Winrar for example can do it, but we will make a portable utility, that is to say that does not require installation and contains only a small file. Unlike other FileProtector's, it will not clearly indicate that it is one, it will display a default error message, letting others believe it is a mundane program.
The main purpose of this article is to provide you with a nice little project to familiarize yourself with the programming, since practicing is what allows you to learn faster. I also do not allow myself to consider this program as perfect, it has defects, it can be improved, modified or even rewritten in another programming language, and this is precisely what allows to practice and learn. Do not hesitate to suggest additions / modifications / improvements, because everyone can learn from others.
Example of operation
In order to make you understand how it works, nothing better than a video demonstration.
Explanations of the demonstration:
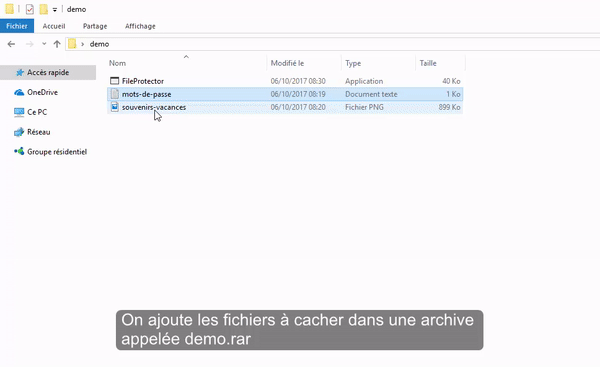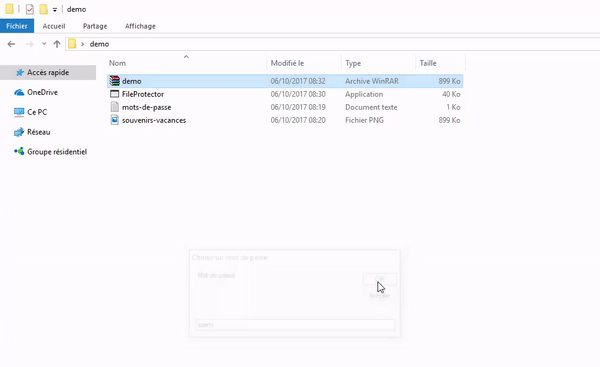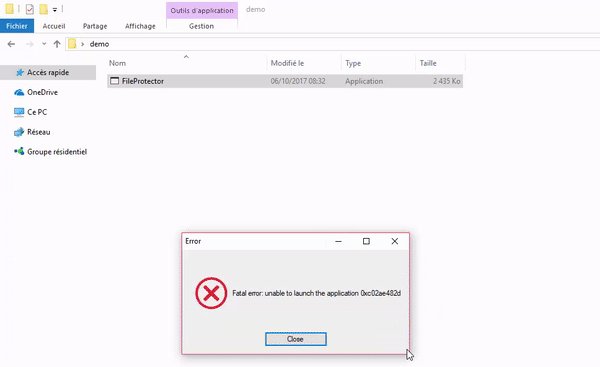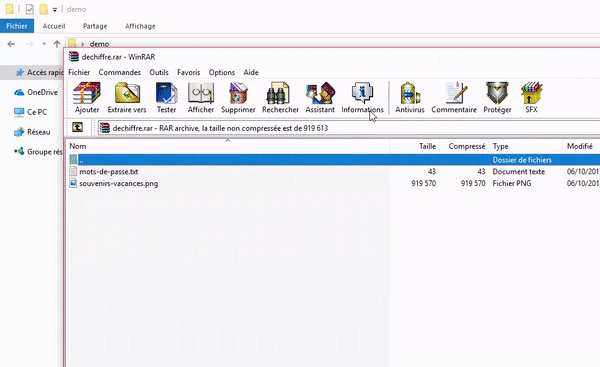
- We have two files to protect that we place in a demo.rar file.
- Drag and drop this demo.rar file into FileProtector.
- FileProtector asks us for a password and demo.rar number.
- We delete the original files and demo.rar
- Then click on FileProtector which displays a false error message.
- In the right corner of the error message, you can display the dialog box to decrypt the file.
- We give back the password and FileProtector we recreate the file demo.rar called this time dechiffre.rar and containing the initial files.
How to program FileProtector?
Let's start from a very general point of view.
There are two ways to use FileProtector
To encrypt
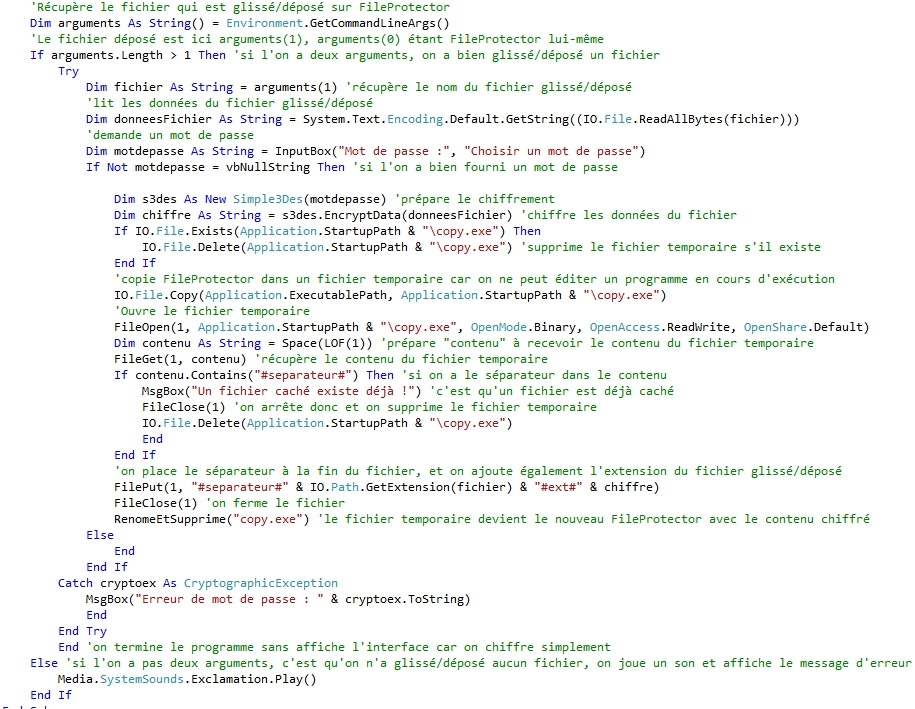
Drag and drop the file to be encrypted on FileProtector. This is handled via Environment.GetCommandLineArgs () which retrieves the full path of the dragged / dropped file.
We then read the contents of the dragged / dropped file with System.Text.Encoding.Default.GetString ((IO.File.ReadAllBytes (file))) and we ask for a password to encrypt all its contents with InputBox.
We now want to add the contents of the encrypted file to the end of FileProtector (the latter thus plays the role of encrypted file container).
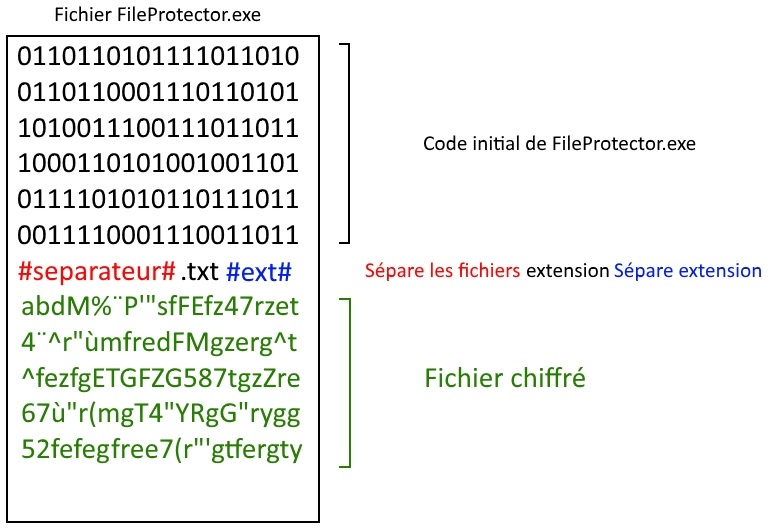
For this we will first add a separator that will allow us to separate the contents of FileProtector contents of the encrypted file. We will also add the extension of the encrypted file so that it can be deciphered with the correct extension later:
FilePut(1, "#separateur#" & IO.Path.GetExtension(fichier) & "#ext#" & chiffre)
Here is a schema that shows the contents of FileProtector when it hides an encrypted file:
But to add this data in FileProtector, we have to go through a temporary copy of FileProtector because it is already running and we can not edit a file that is running.
We will create a temporary file identical to FileProtector, called "copy.exe" and we will add the information in question:
FileOpen(1, Application.StartupPath & "\copy.exe", OpenMode.Binary, OpenAccess.ReadWrite, OpenShare.Default)
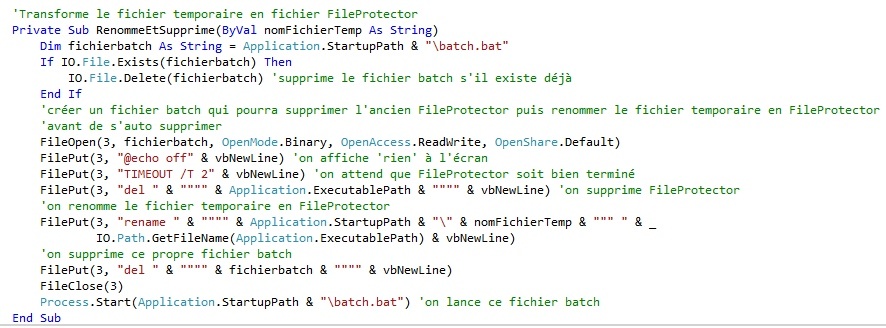
Finally, it will remain to delete the old FileProtector and rename copy.exe FileProtector.exe. It is a combination to keep a single file FileProtector.exe by bypassing the limits mentioned above. For this, we use another temporary file that is a series of batch command to do the actions cited and self-delete.
Here is the source code that starts when FileProtector starts:
Here is the Rename And Delete procedure which is perhaps the most ambiguous part of this program:
To decipher:
FileProtector must be started as a normal program. This will display an error message to keep curious users away.
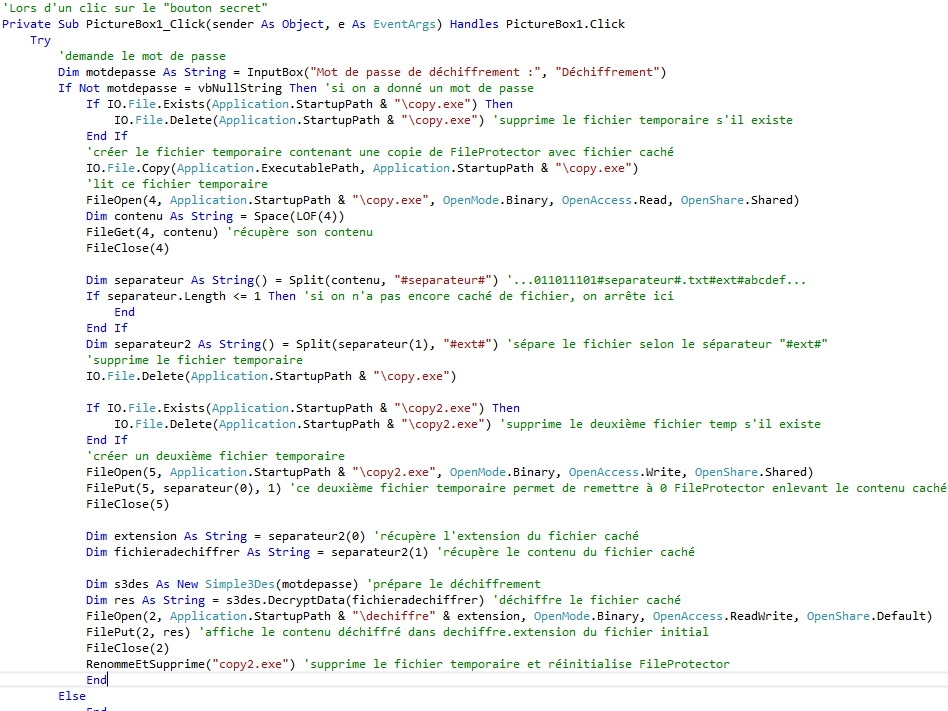
But it has a hidden feature to enable decryption. This is a small, transparent image in the lower right corner of the window.
Clicking on this image displays a dialog asking for the password to decrypt the hidden file.
The decryption then takes place, we do the same thing as before: we create a temporary copy file of FileProtector.exe to recover the encrypted content.
We decipher this content and recreate an empty FileProtector.exe file and the decrypted initial file, with the correct extension.
We reuse a batch file for that.
We can then repeat the steps and encrypt a new file.
Here is the code that executes when you click on the hidden image:
Known limitations
You can only put one file at a time in FileProtector (use a .zip file to place several files).
Files or folders with accents "é, è, à, etc" as well as network paths make (or can make) crash the program.
If the decryption password is incorrect, the temporary copy is not deleted.
The source code can (largely) be improved.
Maximum size tested: 400MB (the speed of (un) encryption and the final size depends on the encryption algorithm used).
Your antivirus may suspect this utility but it is not malicious. In this regard, sandboxed executions prevent the program from running normally.
Supplied as such, without warranty.
Improvements Track
Save the file name with the extension, to recover exactly the same file after decryption.
Manage the character problem (?).
Create an external process to avoid the (ugly) use of a bat file that opens a command prompt.
Check that it works on other systems.
Use more recent libraries / functions than FileOpen, FilePut ... Etc. For example, IO.FileStream and IO.StreamWriter.
Suggest another way to display the decryption dialog.
For example with a keyboard shortcut:
Private Sub Form1_KeyDown(sender As Object, e As KeyEventArgs) Handles Me.KeyDown
If e.Control AndAlso e.KeyCode = Keys.S Then 'si la touche controle est appuyée ainsi que la touche S
'demander mot de passe
End If
End Sub









/cdn.vox-cdn.com/uploads/chorus_image/image/57586139/undefined.0.png)