If it does not shine by its speed or its price, PrivateVPN Trunkspace promises a strong protection of privacy.
The name PrivateVPN is not unknown, but the latest service from Trunkspace Hosting should not be confused with the Swedish site PrivateVPN.com. The Trunkspace service makes it easy to connect to servers in 48 countries.
Features and services
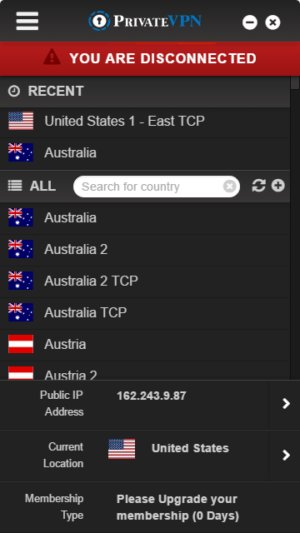
The Windows Trunkspace VPN offers a single panel interface listing all supported national connections. The VPN usually offers at least two possible choices per country. To connect to a specific server, simply select it and click the Connect / Disconnect button to the right of the country name.
A bar at the top of the window is colored red to indicate that there is no connection in progress, it turns yellow when the VPN establishes a connection and green when the connection is active. In the "Settings", which are accessed by the menu icon located in the upper left corner, there are additional options. The Stealth VPN check box is used to hide traffic to bypass network firewalls that block VPN connections.
In "Advanced Setup" on the "Settings" page, there is an option to disable the Internet at logoff, cutting off any Internet access when the VPN connection is interrupted. Finally, in "Routing", it is possible to specify that only certain domains can pass through the VPN. This option is useful if you only want to protect the connection to an enterprise mailbox, for example, while maintaining occasional browsing outside the VPN. The routing function is not particularly difficult to use, but it is rather reserved for experienced users.
Strangely, Trunkspace chose not to add the app icon to the taskbar. To make it appear, you must open the system tray, then click on the icon to display the application in the foreground. When our colleagues asked Trunkspace CEO Atif Khan why he chose this approach, he replied that many Trunkspace customers preferred not to have a VPN icon in the taskbar. "From our experience and from what we've seen, the VPN is typically like" set and forget ". Many of our early customers have complained about finding the icon in the taskbar, because it's not an application like Microsoft Word, an email client, or a web browser that you need to interact with. permanently ".
Performance
Trunkspace's performance was good in some cases, but overall not as good as other services. According to tests of our colleagues at PCWorld, PrivateVPN's speed averaged 19.26%. This is not high considering that the performance of the best services tested reaches 50% and the average performance of all VPNs tested is about 30%. But that does not mean that Trunkspace speeds are not fast. As the testers state, most PrivateVPN scores are double-digit, but not high enough to score better. However, as usual, everyone's experience may vary depending on the ISP, the router and the devices.
Confidentiality, anonymity and trust
Trunkspace is officially based in Montreal. The service is domiciled in a UPS shop in the city, but it's not unusual for a small company whose employees work remotely. The CEO of Trunkspace is, as mentioned before, Atif Khan, and the technical director is Jessica Chan. The Trunkspace Privacy Policy or Terms of Service do not contain any logging commitment. But the homepage of the VPN indicates that it does not record any "personal information" such as "IP addresses, connection and disconnect timestamps, bandwidth consumption, and DNS queries".
It's a good thing to find this information somewhere, but presented as it is, it has more marketing argument than opposable engagement. Trunkspace has recognized the nuance and plans to include these elements in its privacy policy or terms of service in the coming weeks. To register with Trunkspace PrivateVPN, you must also provide the company with more information than many other services claim, including its name, email address, postal address and phone number, regardless of the mode. of payment. Trunkspace accepts payments by PayPal, credit card, bank transfer, gift cards, and several cryptocurrencies.
Conclusion
The VPN approach of Trunkspace is clear. The service does not offer additional features like some VPNs, and its speeds are acceptable, but not exceptional. But, given the offer, the price is a bit too high. There are cheaper solutions on the market with similar privacy policies that require less personal information at registration. PrivateVPN's privacy policy commitments are significant. And if the service revised its tariff down and required less personal information, PC World testers would recommend it more strongly.